Tryhackme Bounty Hunter
Walkthrough of the Linux machine Bounty Hunter From Tryhackme
Before Getting Started
This is a Short Room from tryhackme which can completed by tracking down the changes made through version Git is a distributed version-control system for tracking changes in source code during software development. It is designed for coordinating work among programmers, but it can be used to track changes in any set of files.
There is only one task in this room
Our Objective is to obtain the password for the login
As always lets start with our nmap
nmap -sS -A 10.10.47.137
─[zen-prime@zerr0-satellite]─[~/htb/githappens]
└──╼ [★]$ sudo nmap -sS -A 10.10.47.137
[sudo] password for zen-prime:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-13 22:43 IST
Nmap scan report for 10.10.47.137
Host is up (0.22s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.0 (Ubuntu)
| http-git:
| 10.10.47.137:80/.git/
| Git repository found!
|_ Repository description: Unnamed repository; edit this file 'description'
| to name the...
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Super Awesome Site!
No exact OS matches for host (If you know what OS is running on it, see
As nmap shows that there is only one service is running on this machine 80 http
also nmap found a directory called .git and it is Git Repository
Lets First Check our Index Page
It just shows a Simple Login Page
I tried some default credentials for this page but nothing happends
Let move on to the next
From Nmap result we identify a hidden directory called .git which reveals that it is Github Repository
so lets check that out
Here we use a tool called Git Dumper to clone this repository to our local machine which will help us look around on it.
or We can simply use our wget command also to download this report
wget -m -I .git http://10.10.47.137/.git
Here
-m : <To mirror the directory, –mirror
-I : list of allowed directories
We can use tool at this time
after downloading the tool . Let start cloneing
./git-dumper.py http://10.10.47.137/.git git-dump
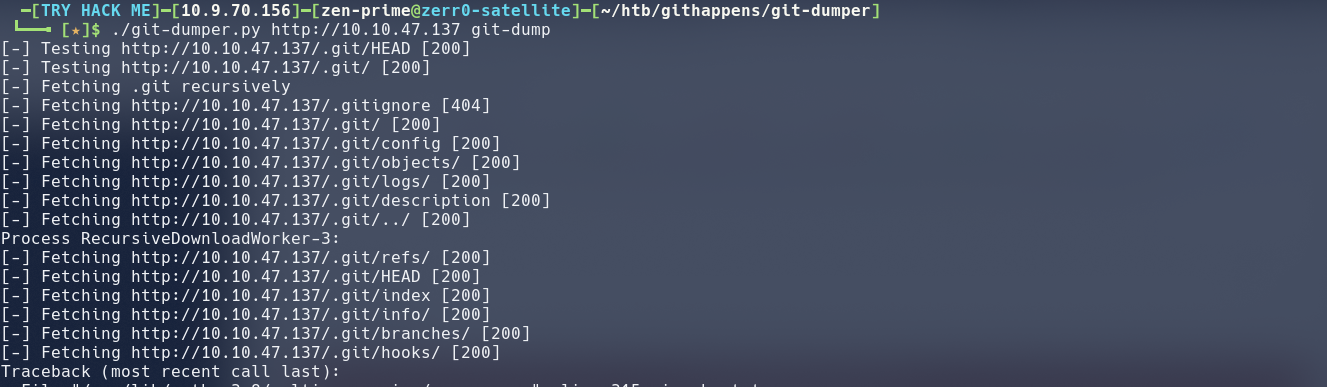
It will take some few minutes to completly clone the repository
Now using the git command we can now successfully look this repository
git log
──[zen-prime@zerr0-satellite]─[~/htb/githappens/git-dumper/git-dump/.git]
└──╼ [★]$ git log
commit d0b3578a628889f38c0affb1b75457146a4678e5 (HEAD -> master, tag: v1.0)
Author: Adam Bertrand <hydragyrum@gmail.com>
Date: Thu Jul 23 22:22:16 2020 +0000
Update .gitlab-ci.yml
commit 77aab78e2624ec9400f9ed3f43a6f0c942eeb82d
Author: Hydragyrum <hydragyrum@gmail.com>
Date: Fri Jul 24 00:21:25 2020 +0200
add gitlab-ci config to build docker file.
commit 2eb93ac3534155069a8ef59cb25b9c1971d5d199
Author: Hydragyrum <hydragyrum@gmail.com>
Date: Fri Jul 24 00:08:38 2020 +0200
setup dockerfile and setup defaults.
commit d6df4000639981d032f628af2b4d03b8eff31213
Author: Hydragyrum <hydragyrum@gmail.com>
Date: Thu Jul 23 23:42:30 2020 +0200
Make sure the css is standard-ish!
commit d954a99b96ff11c37a558a5d93ce52d0f3702a7d
Author: Hydragyrum <hydragyrum@gmail.com>
Date: Thu Jul 23 23:41:12 2020 +0200
re-obfuscating the code to be really secure!
commit bc8054d9d95854d278359a432b6d97c27e24061d
Author: Hydragyrum <hydragyrum@gmail.com>
Date: Thu Jul 23 23:37:32 2020 +0200
Security says obfuscation isn't enough.
commit e56eaa8e29b589976f33d76bc58a0c4dfb9315b1
Author: Hydragyrum <hydragyrum@gmail.com>
Date: Thu Jul 23 23:25:52 2020 +0200
Obfuscated the source code.
Hopefully security will be happy!
commit 395e087334d613d5e423cdf8f7be27196a360459
Author: Hydragyrum <hydragyrum@gmail.com>
Date: Thu Jul 23 23:17:43 2020 +0200
Made the login page, boss!
commit 2f423697bf81fe5956684f66fb6fc6596a1903cc
Author: Adam Bertrand <hydragyrum@gmail.com>
Date: Mon Jul 20 20:46:28 2020 +0000
Initial commit
From the commits e56eaa8e29b589976f33d76bc58a0c4dfb9315b1 &
e56eaa8e29b589976f33d76bc58a0c4dfb9315b1
we can understand that the source code is obsulated there. so lets check
the previous commit 395e087334d613d5e423cdf8f7be27196a360459 done by the Author
which also shows that the Login Page is Maded.
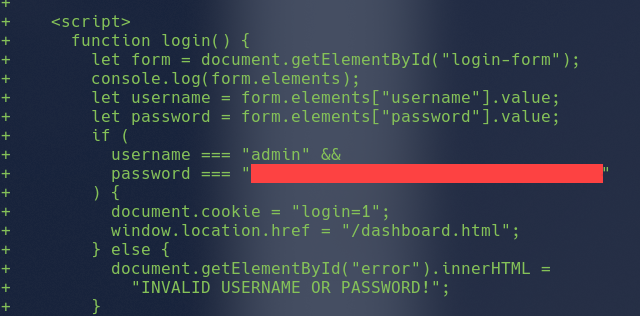
git show 395e087334d613d5e423cdf8f7be27196a360459
Looking at the result and scrolling through it we can see a login() written in javascript which reveals
the Password for the Login Page.
The Room was great .Keep in mind that nowdays many websites exposes the .git repositories to public.
So cloneing or mirroring these repo can lead exposes the contents inside it. It is better to delete these git from the webserver to
ensure the Security.
Hope We learned something new from this.
</strong>Thanks</strong>
