Tryhackme Walkthrough of Git Happens
Walkthrough of the machine Git Happens From Tryhackme
This writeup is about challenge C4ptur3-th3-fl4g in Tryhackme Platform . In this writeup I am going to explain how the challenge/Tasks can be solved.
The First task of this challenge can be solved by decoding the chipers such as ROT13 , Base64 , Base32 , Morse code and binary. In this challenge all the Answers are Case Sensitive.
### Task 1
The task 1 Cipher is known l337 code. which be solved by simpling guessing it or using any online converters
Cipher : c4n y0u c4p7u23 7h3 f149?
Answer : can you capture the flag?
### Task 2 In this Task the Cipher is an binary code, which can either be solved using an Online Converter
Cipher :
01101100 01100101 01110100 01110011 00100000
01110100 01110010 01111001 00100000 01110011
01101111 01101101 01100101 00100000 01100010
01101001 01101110 01100001 01110010 01111001
00100000 01101111 01110101 01110100 00100001
Answer : lets try some binary out!
The 3rd Task is to deal with the Cipher base32. An base32 is numeral system of base 32. which uses set 32 digits .with 26 upper-case letter A-Z and the digits range from 2-7.
This challenge can solved using an online converter or using the command line
Cipher : MJQXGZJTGIQGS4ZAON2XAZLSEBRW63LNN5XCA2LOEBBVIRRHOM======
Command :
echo "MJQXGZJTGIQGS4ZAON2XAZLSEBRW63LNN5XCA2LOEBBVIRRHOM======" | base32 -d 
Answer : base32 is super common in CTF’s
In this we can see base64 chipher which realy common in almost all CTF challenges This can be also decoded using any online base64 decoder or using Command Line
Cipher :
RWFjaCBCYXNlNjQgZGlnaXQgcmVwcmVzZW50cyBleGFjdGx5IDYgYml0cyBvZiBkYXRhLg==
Command :
echo "RWFjaCBCYXNlNjQgZGlnaXQgcmVwcmVzZW50cyBleGFjdGx5IDYgYml0cyBvZiBkYXRhLg==" | base64 -d 
Answer : Each Base64 digit represents exactly 6 bits of data.
Here the Cipher is an Hexadecimal , An hex is also known as base16 which consits of 16 bit binary.
We can also use the Online Converter this converter to solve the challenge or using xxd command to convert it to ascii form.
Cipher : 68 65 78 61 64 65 63 69 6d 61 6c 20 6f 72 20 62 61 73 65 31 36 3f
Command :
echo -e 68 65 78 61 64 65 63 69 6d 61 6c 20 6f 72 20 62 61 73 65 31 36 3f | xxd -r -p  <strong>Answer</strong> : hexadecimal or base16?
The Task is to convert an ROT13 Cipher to ascii. in Rot13 each letter on a phrase is “rotated” 13 times.
An online converter is available to convert this rot13 cipher. or can use the command
Cipher : Ebgngr zr 13 cynprf!
Command :
echo "Ebgngr zr 13 cynprf!" | tr '[A-Za-z]' '[N-ZA-Mn-za-m]'
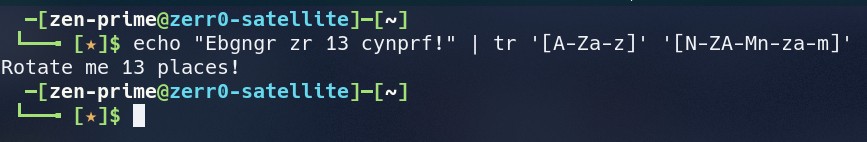
Answer : Rotate me 13 places!
The rot47 is also known as rotate 47. where the all the letters are rotated in 47 times it is also like the cipher ro13 but this contain all the characters in ascii including digits and Punctuations
we can use Rot47 online decoder to solve this challenge
Cipher : *@F DA:? >6 C:89E C@F?5 323J C:89E C@F?5 Wcf E:>6DX
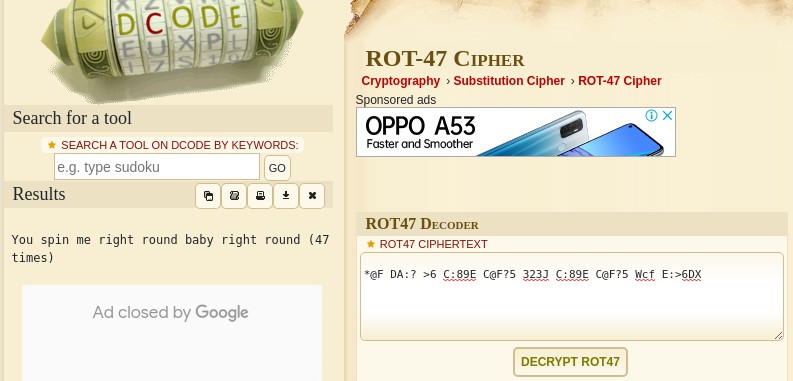
Answer : You spin me right round baby right round (47 times)
This task is to deal with Morse Code. with dashes and dotes
we can solve it using this morsecodedecoder
Cipher : - . .-.. . -.-. — – – ..- -. .. -.-. .- - .. — -. . -. -.-. — -.. .. -. –.
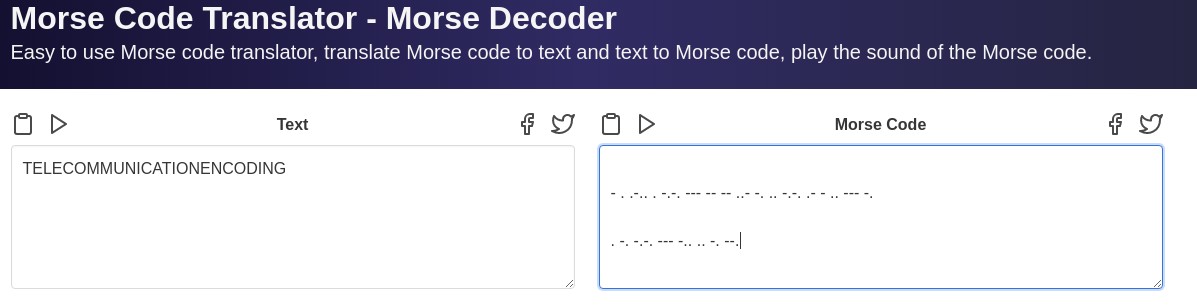
Answer : TELECOMMUNICATIONENCODING
Here we can see a BCD known Binary Coded Decimal . In an BCD each number represent it binary value. which is further converted to ascii to get series of letter.
Here i used an Online Converter Cryptii to solve this one
Cipher : 85 110 112 97 99 107 32 116 104 105 115 32 66 67 68
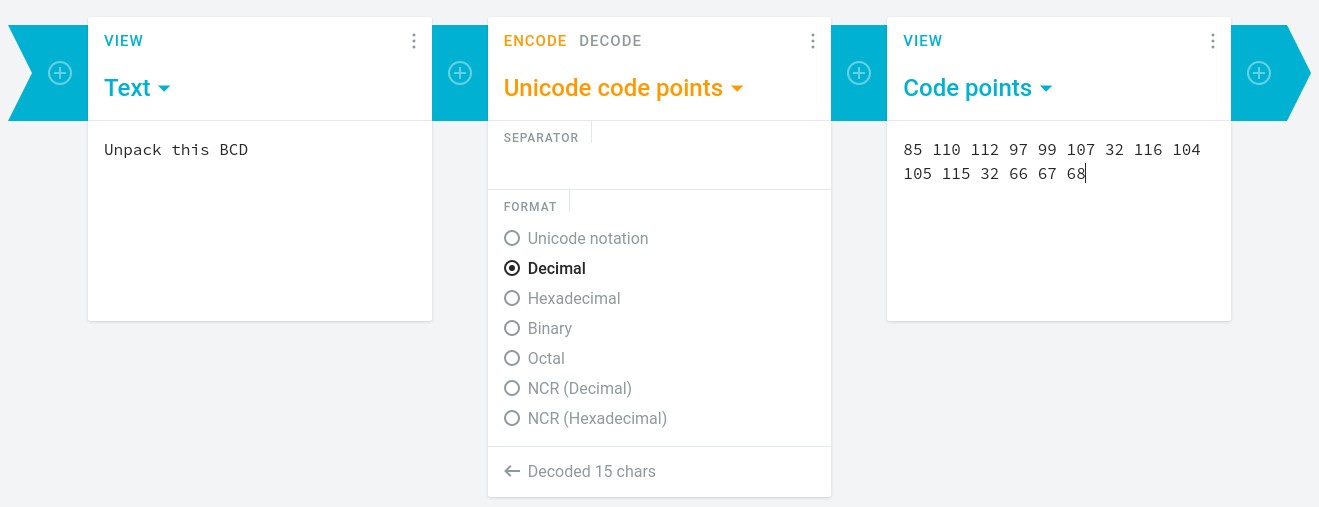
Answer : Unpack this BCD
This is the last task of Transalation and Shifting in this challenge . This task is the combination of all the above task that we done . which is a super cool but is little trickier.
It is an base64 encoded . To get the Answer First
Decode this base64
Then a morse code is obtained.
Decode that Morse Code
An binary code will obtain
Decode that Binary Code to ascii
we get ROT47
Decode the Rot47
An Decimal value will obtain
Decode this Decimal Value to Ascii to obtain the Final Answer
Answer : Let’s make this a bit trickier…
In this challenge Phase we have to deal with something called Spectrograms .
A spectrogram is a visual representation of the spectrum of frequencies of a signal as it varies with time. When applied to an audio signal, spectrograms are sometimes called sonographs, voiceprints, or voicegrams. When the data is represented in a 3D plot they may be called waterfalls.
Use the Tool called Audacity it will available in the Linux repo or Download it directly from their Site
First Open the Downloaded Audio Clip in Audacity.
use Shift + M to open the options menu
Under this menu click on the option called Spectrogram
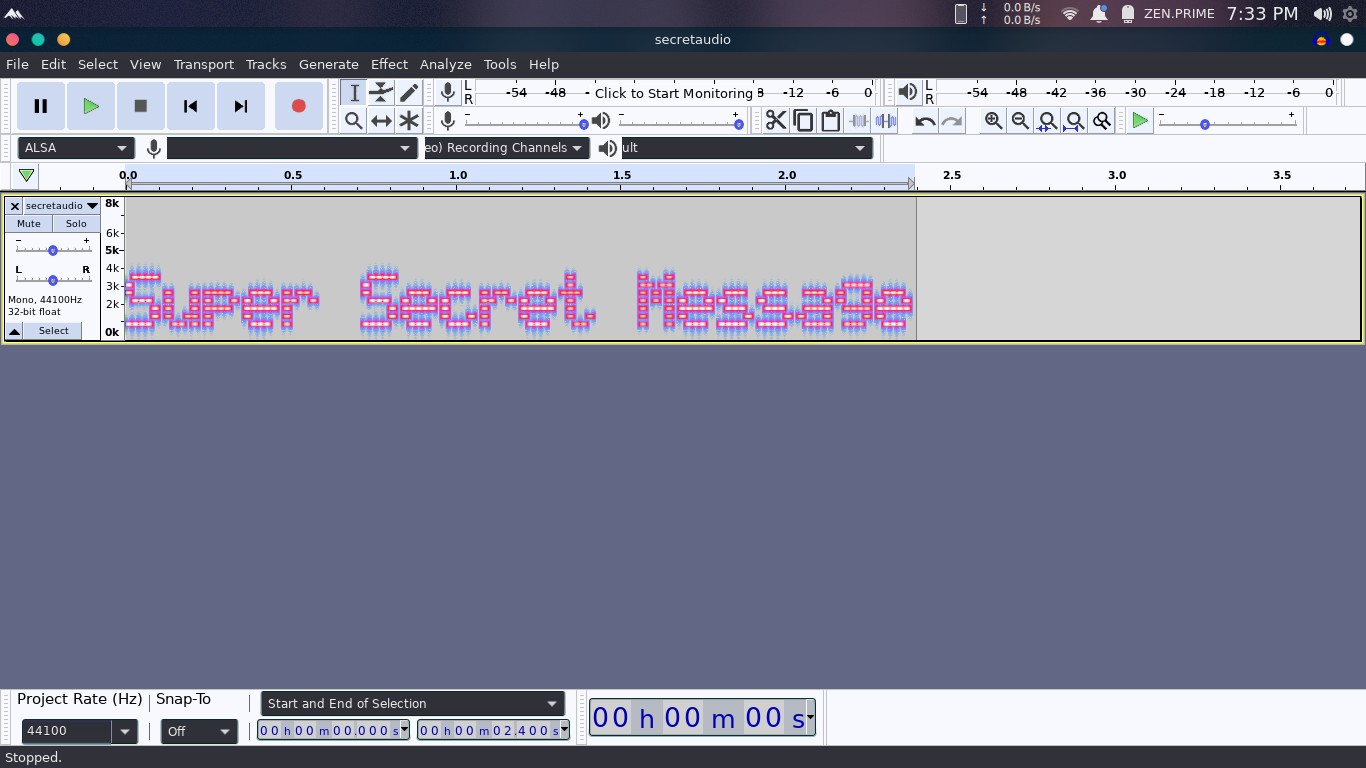
Bingoo We Got The Answer For this task.
Answer : Super Secret Message
Steganography is a method used to hide a file such as images,messages,audios, videos in another file such like images,audios,videos
In this task first we need to download the image from the tryhackme room

The image will look like this.
Use the tool called steghide to extract the data from the image
Command :
steghide extract -sf stegosteg.jpg
use the above command and just give blank password for passphrase
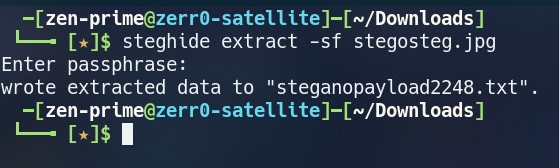
The Data will extract to the file called steganopayload2248.txt
Open that File to obtain the Answer
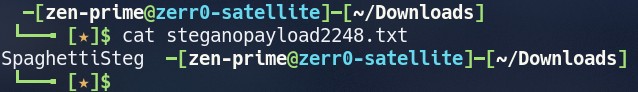
Answer : SpaghettiSteg
This is the last part of this challenge . In this part there is only 2 task that we need to solve
Task1
Download and get ‘inside’ the file. What is the first filename & extension?
*Task2 Get inside the archive and inspect the file carefully. Find the hidden text.?
To complete this task first we need to download the file from the Room.
Task 1 : Download and get ‘inside’ the file. What is the first filename & extension?
From the Above question we can understand that something is present inside that downloaded file.
To get the hidden text from the file i just simply run the string command against this Image and got that Two Flags.
strings meme.jpg
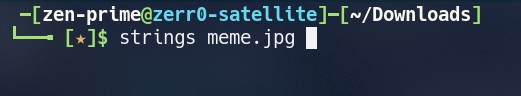

Answer 1 : hackerchat.png
Answer 2 : AHH_YOU_FOUND_ME!
The Challenge was supercool and absolutely Best For the beginners. This covers the basics of Ciphers that common in all the CTF challenges.
